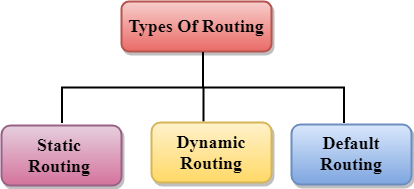
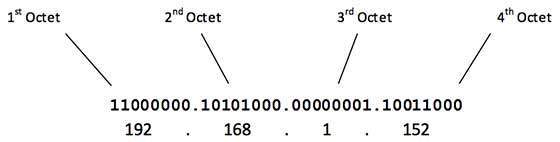
Network Technology
UNIT - 1
=>Advanced Network Topologies Ethernet, CDDI, FDDI
- Ethernet is a way of connecting computers together in a local area network or LAN. It has been the most widely used method of linking computers together in LANs since the 1990s.
- The basic idea of its design is that multiple computers have access to it and can send data at any time.
- It was commercially introduced in 1980 and first standardized in 1983 as IEEE 802.3, and has since been refined to support higher bit rates and longer link distances.
- Over time, Ethernet has largely replaced competing wired LAN technologies such as token ring, FDDI and ARCNET.
- Ethernet evolved to include higher bandwidth, improved media access control methods, and different physical media. The coaxial cable was replaced with point-to-point links connected by Ethernet repeaters or switches.
- For a local area network (LAN), CDDI (Copper Distributed Data Interface) is a standard for data transmission based on FDDI (Fiber Distributed Data Interface) that uses shielded twisted-pair (STP) or unshielded twisted pair (UTP) copper wire instead of fiber optic lines.
- CDDI supports a dual-ring capacity of 200 Mbps. CDDI's maximum distance is up to 200 meters, which is much shorter than FDDI.
- CDDI is defined by the American National Standards Committee X3-T9.5 and conforms to the Open Systems Interconnection (OSI) model of functional layering. CDDI is officially named the Twisted-Pair Physical Medium Dependent (TP-PMD) standard and is also referred to as Twisted Pair Distributed Data Interface (TP-DDI).
- Fiber Distributed Data Interface (FDDI) is a standard for data transmission in a local area network. It uses optical fiber as its standard underlying physical medium, although it was also later specified to use copper cable, in which case it may be called CDDI (Copper Distributed Data Interface).
Preamble: 1 byte for synchronization.
Start Delimiter: 1 byte that marks the beginning of the frame.
Frame Control: 1 byte that specifies whether this is a data frame or control frame.
Destination Address: 2-6 bytes that specifies address of destination station.
Source Address: 2-6 bytes that specifies address of source station.
Payload: A variable length field that carries the data from the network layer.
- Checksum: 4 bytes frame check sequence for error detection.
- Anycast addressing routes datagrams to a single member of agroup of potential receivers that are all identified by the samedestination address. This is a one-to-nearest association.
- Broadcast addressing uses a one-to-many association,datagrams are routed from a single sender to multipleendpoints simultaneously in a single transmission. The networkautomatically replicates datagrams as needed for all networksegments (links) that contain an eligible receiver.
- Multicast addressing uses a one-to-unique many association,datagrams are routed from a single sender to multiple selectedendpoints simultaneously in a single transmission.
- Unicast addressing uses a one-to-one association betweendestination address and network endpoint: each destinationaddress uniquely identifies a single receiver endpoint.
- Geocast refers to the delivery of information to a group ofdestinations in a network identified by their geographicallocations. It is a specialized form of Multicast addressing usedby some routing protocols for mobile ad hoc networks.
TCP/IP model
|
Network Access Layer
- A network layer is the lowest layer of the TCP/IP model.
- A network layer is the combination of the Physical layer and Data Link layer defined in the OSI reference model.
- It defines how the data should be sent physically through the network.
- This layer is mainly responsible for the transmission of the data between two devices on the same network.
- The functions carried out by this layer are encapsulating the IP datagram into frames transmitted by the network and mapping of IP addresses into physical addresses.
- The protocols used by this layer are ethernet, token ring, FDDI, X.25, frame relay.
Types of Transmission Media
Guided Media
- It is defined as the physical medium through which the signals are transmitted. It is also known as Bounded media.
Twisted pair:
- Twisted pair is a physical media made up of a pair of cables twisted with each other. A twisted pair cable is cheap as compared to other transmission media. Installation of the twisted pair cable is easy, and it is a lightweight cable. The frequency range for twisted pair cable is from 0 to 3.5KHz
- A twisted pair consists of two insulated copper wires arranged in a regular spiral pattern.
- The degree of reduction in noise interference is determined by the number of turns per foot. Increasing the number of turns per foot decreases noise interference.
Unshielded Twisted Pair:
An unshielded twisted pair is widely used in telecommunication. Following are the categories of the unshielded twisted pair cable:
- Category 1: Category 1 is used for telephone lines that have low-speed data.
- Category 2: It can support upto 4Mbps.
- Category 3: It can support upto 16Mbps.
- Category 4: It can support upto 20Mbps. Therefore, it can be used for long-distance communication.
- Category 5: It can support upto 200Mbps.
Advantages Of Unshielded Twisted Pair:
- It is cheap.
- Installation of the unshielded twisted pair is easy.
- It can be used for high-speed LAN.
Disadvantage:
- This cable can only be used for shorter distances because of attenuation.
Shielded Twisted Pair
A shielded twisted pair is a cable that contains the mesh surrounding the wire that allows the higher transmission rate.
Characteristics Of Shielded Twisted Pair:
- The cost of the shielded twisted pair cable is not very high and not very low.
- An installation of STP is easy.
- It has higher capacity as compared to unshielded twisted pair cable.
- It has a higher attenuation.
- It is shielded that provides the higher data transmission rate.
Disadvantages
- It is more expensive as compared to UTP and coaxial cable.
- It has a higher attenuation rate.
Wire Cutter: - To cut the network cable of the required length from the bundle, you can use any standard wire cutter tool or can use a wire cutter tool that is specially designed for the twisted-pair cable. A twisted-pair wire cutter usually includes additional blades for stripping the wire.
Wire Stripper: - This tool is used to remove the outer and inner jackets of the network cable. Typically, you do not need to purchase this tool separately as all standard twisted-pair wire cutters are equipped with wire-strippers.
Crimp tool: - This tool is used to attach the connectors to the cable. Typically, this tool also includes a wire-cutter and wire-stripper. So if you have crimp tool, you don't have need to wire-cutter and wire-striper separately.
Coaxial Cable
- Coaxial cable is very commonly used transmission media, for example, TV wire is usually a coaxial cable.
- The name of the cable is coaxial as it contains two conductors parallel to each other.
- It has a higher frequency as compared to Twisted pair cable.
- The inner conductor of the coaxial cable is made up of copper, and the outer conductor is made up of copper mesh. The middle core is made up of non-conductive cover that separates the inner conductor from the outer conductor.
- The middle core is responsible for the data transferring whereas the copper mesh prevents from the EMI(Electromagnetic interference).
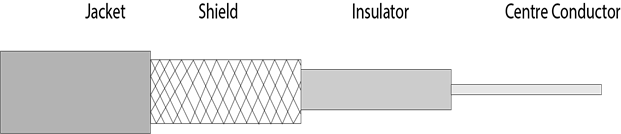
Coaxial cable is of two types:
- Baseband transmission: It is defined as the process of transmitting a single signal at high speed.
- Broadband transmission: It is defined as the process of transmitting multiple signals simultaneously.
Advantages Of Coaxial cable:
- The data can be transmitted at high speed.
- It has better shielding as compared to twisted pair cable.
- It provides higher bandwidth.
Disadvantages Of Coaxial cable:
- It is more expensive as compared to twisted pair cable.
- If any fault occurs in the cable causes the failure in the entire network.
Fibre Optic
- Fibre optic cable is a cable that uses electrical signals for communication.
- Fibre optic is a cable that holds the optical fibres coated in plastic that are used to send the data by pulses of light.
- The plastic coating protects the optical fibres from heat, cold, electromagnetic interference from other types of wiring.
- Fibre optics provide faster data transmission than copper wires.
Diagrammatic representation of fibre optic cable:
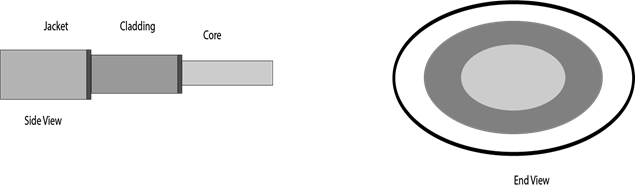
Basic elements of Fibre optic cable:
- Core: The optical fibre consists of a narrow strand of glass or plastic known as a core. A core is a light transmission area of the fibre. The more the area of the core, the more light will be transmitted into the fibre.
- Cladding: The concentric layer of glass is known as cladding. The main functionality of the cladding is to provide the lower refractive index at the core interface as to cause the reflection within the core so that the light waves are transmitted through the fibre.
- Jacket: The protective coating consisting of plastic is known as a jacket. The main purpose of a jacket is to preserve the fibre strength, absorb shock and extra fibre protection.
Following are the advantages of fibre optic cable over copper:
- Greater Bandwidth: The fibre optic cable provides more bandwidth as compared copper. Therefore, the fibre optic carries more data as compared to copper cable.
- Faster speed: Fibre optic cable carries the data in the form of light. This allows the fibre optic cable to carry the signals at a higher speed.
- Longer distances: The fibre optic cable carries the data at a longer distance as compared to copper cable.
- Better reliability: The fibre optic cable is more reliable than the copper cable as it is immune to any temperature changes while it can cause obstruct in the connectivity of copper cable.
- Thinner and Sturdier: Fibre optic cable is thinner and lighter in weight so it can withstand more pull pressure than copper cable.
UnGuided Transmission
- An unguided transmission transmits the electromagnetic waves without using any physical medium. Therefore it is also known as wireless transmission.
- In unguided media, air is the media through which the electromagnetic energy can flow easily.
Unguided transmission is broadly classified into three categories:
Radio waves
- Radio waves are the electromagnetic waves that are transmitted in all the directions of free space.
- Radio waves are omnidirectional, i.e., the signals are propagated in all the directions.
- The range in frequencies of radio waves is from 3Khz to 1 khz.
- In the case of radio waves, the sending and receiving antenna are not aligned, i.e., the wave sent by the sending antenna can be received by any receiving antenna.
- An example of the radio wave is FM radio.
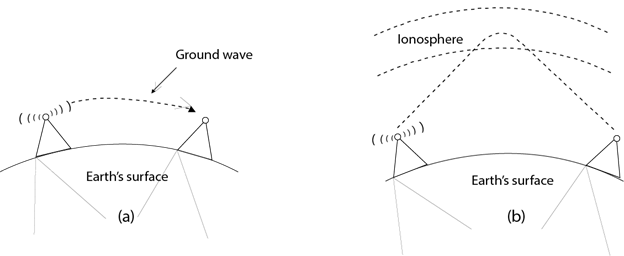
Applications Of Radio waves:
- A Radio wave is useful for multicasting when there is one sender and many receivers.
- An FM radio, television, cordless phones are examples of a radio wave.
Advantages Of Radio transmission:
- Radio transmission is mainly used for wide area networks and mobile cellular phones.
- Radio waves cover a large area, and they can penetrate the walls.
- Radio transmission provides a higher transmission rate.
Microwaves
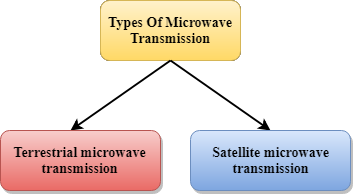
Microwaves are of two types:
- Terrestrial microwave
- Satellite microwave communication.
Terrestrial Microwave Transmission
- Terrestrial Microwave transmission is a technology that transmits the focused beam of a radio signal from one ground-based microwave transmission antenna to another.
- Microwaves are the electromagnetic waves having the frequency in the range from 1GHz to 1000 GHz.
- Microwaves are unidirectional as the sending and receiving antenna is to be aligned, i.e., the waves sent by the sending antenna are narrowly focussed.
- In this case, antennas are mounted on the towers to send a beam to another antenna which is km away.
- It works on the line of sight transmission, i.e., the antennas mounted on the towers are the direct sight of each other.
Characteristics of Microwave:
- Frequency range: The frequency range of terrestrial microwave is from 4-6 GHz to 21-23 GHz.
- Bandwidth: It supports the bandwidth from 1 to 10 Mbps.
- Short distance: It is inexpensive for short distance.
- Long distance: It is expensive as it requires a higher tower for a longer distance.
- Attenuation: Attenuation means loss of signal. It is affected by environmental conditions and antenna size.
Advantages Of Microwave:
- Microwave transmission is cheaper than using cables.
- It is free from land acquisition as it does not require any land for the installation of cables.
- Microwave transmission provides an easy communication in terrains as the installation of cable in terrain is quite a difficult task.
- Communication over oceans can be achieved by using microwave transmission.
Disadvantages of Microwave transmission:
- Eavesdropping: An eavesdropping creates insecure communication. Any malicious user can catch the signal in the air by using its own antenna.
- Out of phase signal: A signal can be moved out of phase by using microwave transmission.
- Susceptible to weather condition: A microwave transmission is susceptible to weather condition. This means that any environmental change such as rain, wind can distort the signal.
- Bandwidth limited: Allocation of bandwidth is limited in the case of microwave transmission.
Satellite Microwave Communication
- A satellite is a physical object that revolves around the earth at a known height.
- Satellite communication is more reliable nowadays as it offers more flexibility than cable and fibre optic systems.
- We can communicate with any point on the globe by using satellite communication.
How Does Satellite work?
The satellite accepts the signal that is transmitted from the earth station, and it amplifies the signal. The amplified signal is retransmitted to another earth station.
Advantages Of Satellite Microwave Communication:
- The coverage area of a satellite microwave is more than the terrestrial microwave.
- The transmission cost of the satellite is independent of the distance from the centre of the coverage area.
- Satellite communication is used in mobile and wireless communication applications.
- It is easy to install.
- It is used in a wide variety of applications such as weather forecasting, radio/TV signal broadcasting, mobile communication, etc.
Disadvantages Of Satellite Microwave Communication:
- Satellite designing and development requires more time and higher cost.
- The Satellite needs to be monitored and controlled on regular periods so that it remains in orbit.
- The life of the satellite is about 12-15 years. Due to this reason, another launch of the satellite has to be planned before it becomes non-functional.
Infrared
- An infrared transmission is a wireless technology used for communication over short ranges.
- The frequency of the infrared in the range from 300 GHz to 400 THz.
- It is used for short-range communication such as data transfer between two cell phones, TV remote operation, data transfer between a computer and cell phone resides in the same closed area.
Characteristics Of Infrared:
- It supports high bandwidth, and hence the data rate will be very high.
- Infrared waves cannot penetrate the walls. Therefore, the infrared communication in one room cannot be interrupted by the nearby rooms.
- An infrared communication provides better security with minimum interference.
- Infrared communication is unreliable outside the building because the sun rays will interfere with the infrared waves.
Multiplexing is a technique used to combine and send the multiple data streams over a single medium. The process of combining the data streams is known as multiplexing and hardware used for multiplexing is known as a multiplexer.
Multiplexing is achieved by using a device called Multiplexer (MUX) that combines n input lines to generate a single output line. Multiplexing follows many-to-one, i.e., n input lines and one output line.
Demultiplexing:
Demultiplexing is achieved by using a device called Demultiplexer (DEMUX) available at the receiving end. DEMUX separates a signal into its component signals (one input and n outputs). Therefore, we can say that demultiplexing follows the one-to-many approach.
UNIT - 2
What is a packet?
In networking, a packet is a small segment of a larger message. Data sent over computer networks*, such as the Internet, is divided into packets. These packets are then recombined by the computer or device that receives them.
What is a protocol?
TCP
TCP stands for Transmission Control Protocol. It is a transport layer protocol that facilitates
Features of TCP protocol
TCP is a transport layer protocol as it is used in transmitting the data from the sender to the receiver.
TCP is a reliable protocol as it follows the flow and error control mechanism.
It is a full-duplex means that the data can transfer in both directions at the same time.
Advantages of TCP
congestion window. Disadvantage of TCPIt increases a large amount of overhead as each segment gets its own TCP header, so fragmentation by the router increases the overhead. |
UDP
Features of UDP protocolThe following are the features of the UDP protocol:
UDP is the simplest transport layer communication protocol. It contains a minimum amount of communication mechanisms.
The UDP is a connectionless protocol as it does not create a virtual path to transfer the data.
In the case of UDP, the datagrams are sent in some order will be received in the same order is not guaranteed as the datagrams are not numbered.
The UDP protocol uses different port numbers so that the data can be sent to the correct destination. The port numbers are defined between 0 and 1023.
UDP enables faster transmission as it is a connectionless protocol, i.e., no virtual path is required to transfer the data.
The UDP does have any acknowledgment mechanism, i.e., there is no handshaking between the UDP sender and UDP receiver.
It is a stateless protocol that means that the sender does not get the acknowledgement for the packet which has been sent. Limitations
Advantages
|







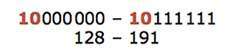
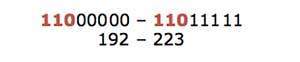
Comments
Post a Comment